[ad_1]
An evaluation of the indications of compromise (IoCs) related to the JumpCloud hack has uncovered proof pointing to the involvement of North Korean state-sponsored teams, in a mode that is harking back to the supply chain attack targeting 3CX.
The findings come from SentinelOne, which mapped out the infrastructure pertaining to the intrusion to uncover underlying patterns. It is value noting that JumpCloud, final week, attributed the assault to an unnamed “refined nation-state sponsored risk actor.”
“The North Korean risk actors exhibit a excessive stage of creativity and strategic consciousness of their focusing on methods,” SentinelOne safety researcher Tom Hegel informed The Hacker Information. “The analysis findings reveal a profitable and multifaceted strategy employed by these actors to infiltrate developer environments.”
“They actively search entry to instruments and networks that may function gateways to extra in depth alternatives. Their tendency to execute a number of ranges of provide chain intrusions earlier than participating in financially motivated theft is noteworthy.”
In a associated growth, CrowdStrike, which is working with JumpCloud to probe the incident, pinned the assault to a North Korean actor referred to as Labyrinth Chollima, a sub cluster inside the notorious Lazarus Group, in line with Reuters.
The infiltration was used as a “springboard” to focus on cryptocurrency corporations, the information company mentioned, indicating an try on a part of the adversary to generate unlawful revenues for the sanctions-hit nation.
The revelations additionally coincide with a low-volume social engineering marketing campaign recognized by GitHub that targets the non-public accounts of staff of know-how corporations, utilizing a mixture of repository invites and malicious npm bundle dependencies. The focused accounts are related to blockchain, cryptocurrency, on-line playing, or cybersecurity sectors.
The Microsoft subsidiary linked the marketing campaign to a North Korean hacking group it tracks beneath the identify Jade Sleet (aka TraderTraitor).
“Jade Sleet largely targets customers related to cryptocurrency and different blockchain-related organizations, but in addition targets distributors utilized by these corporations,” GitHub’s Alexis Wales said in a report printed on July 18, 2023.
The assault chains contain organising bogus personas on GitHub and different social media providers equivalent to LinkedIn, Slack, and Telegram, though in some instances the risk actor is believed to have taken management of respectable accounts.
Below the assumed persona, Jade Sleet initiates contact with the targets and invitations them to collaborate on a GitHub repository, convincing the victims into cloning and working the contents, which characteristic decoy software program with malicious npm dependencies that act as first-stage malware to obtain and execute second-stage payloads on the contaminated machine.
Shield Against Insider Threats: Master SaaS Security Posture Management
Frightened about insider threats? We have got you lined! Be a part of this webinar to discover sensible methods and the secrets and techniques of proactive safety with SaaS Safety Posture Administration.
The malicious npm packages, per GitHub, are a part of a marketing campaign that first got here to gentle final month, when Phylum detailed a provide chain risk involving a singular execution chain that makes use of a pair of fraudulent modules to fetch an unknown piece of malware from a distant server.
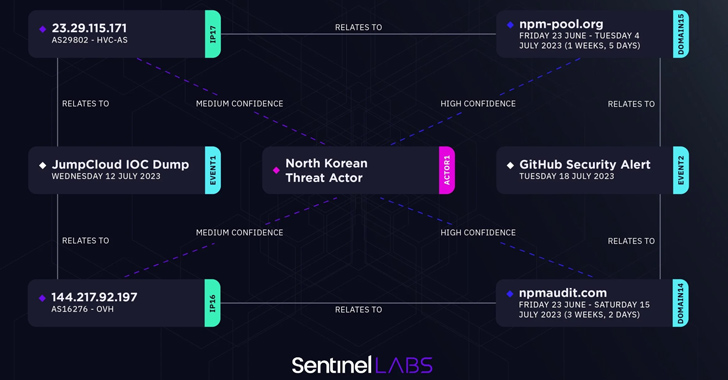
SentinelOne, in its newest evaluation, mentioned 144.217.92[.]197, an IP deal with linked to the JumpCloud assault, resolves to npmaudit[.]com, one of many eight domains listed by GitHub as used to fetch the second-stage malware. A second IP deal with 23.29.115[.]171 maps to npm-pool[.]org.
“It’s evident that North Korean risk actors are constantly adapting and exploring novel strategies to infiltrate focused networks,” Hegel mentioned. “The JumpCloud intrusion serves as a transparent illustration of their inclination in direction of provide chain focusing on, which yields a mess of potential subsequent intrusions.”
“The DPRK demonstrates a profound understanding of the advantages derived from meticulously choosing high-value targets as a pivot level to conduct provide chain assaults into fruitful networks,” Hegel added.
[ad_2]
Source link